Wie bekannt sein dürfte setzte ich auf die Client-Desktop Virtualisierung von VMware – auch bekannt als VMware Horizon (View).
Ein wichtiges Kriterium für die Anwender ist hier sehr oft die Anmeldezeit. Die spielt vor allem bei „floated“ Desktops eine große Rolle, weil alle notwendigen Einstellungen des Benutzers von einem Netzwerklaufwerk auf die frisch erstellte VM kopiert werden müssen. Das dauert unter Umständen und je nach Profilgröße bis zu einer Minute oder länger.
Um die Anmeldedauer zu analysieren gibt es den Weg über die Ereignisanzeige, welchen ich bereits vor ein paar Jahren beschrieb. Für den Einsatz von Horizon View spielt die Bootdauer z.B. jedoch keine große Rolle, da Virtuelle Maschinen je nach Notwendigkeit gestartet werden und in der Regel ein Puffer zum direkten einloggen vorgehalten wird.
Um die Loginzeiten der User in der Horizon View Umgebung zu analysieren wurde bereits vor einiger Zeit der VMware Logon Monitor als Tool des VMware Fling Projektes veröffentlicht.
Seit der Horizon Version 7.1 ist der Logon Monitor jetzt standardmäßig im VMware Horizon Agent enthalten. Er muss lediglich über Registry Keys aktiviert werden.
Geloggt werden unter anderem folgende Werte:
|
|
Wie wird der VMware Logon Monitor aktiviert ?
Es muss der aktuelle VMware View Agent ab Version 7.1 installiert sein. Anschließend wird dieser per Registry konfiguriert. Für meinen Anwendungszweck reicht es aus, einen Netzwerkshare anzugeben auf dem die Logdateien aller VM’s abgespeichert werden:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\VMware, Inc.\VMware Logon Monitor] "flags"=dword:00000003 "RemoteLogPath"="\\ip-network-share\\logs\\view" "RemoteLog"="\\ip-network-share\\logs\\view"
So ganz scheint die offizielle Dokumentation noch nicht angepasst zu sein. Es existiert bisher nur die überschaubare Anleitung des VMware Flings.
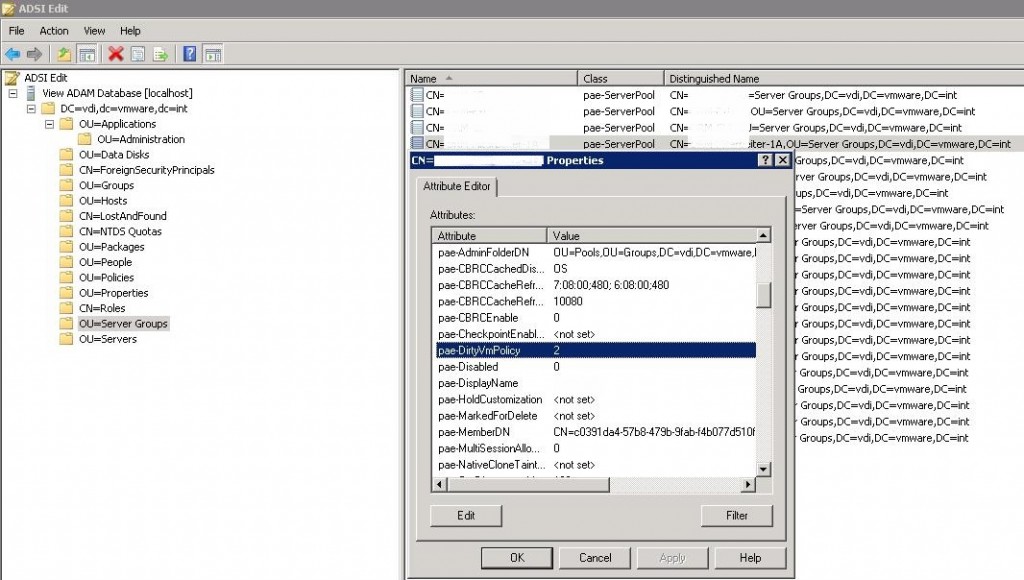
[stextbox id=’info‘]In meinen Test ließen sich die Registry Werte nicht per GPO auf die VM’s anwenden. Sie wurden zwar angewendet, aber der VMware Logon Monitor funktionierte nicht. Nachdem ich die Werte dann im Template gesetzt und den Pool neu ausgerollt habe, funktionierte es auf Anhieb.[/stextbox]
Aufbau der Log-Datei
Ist der VMware Logon Monitor per Registry aktiviert und es hat sich ein Benutzer angemeldet, finden sich die Log-Dateien unter:
C:\ProgramData\VMware\VMware Logon Monitor\logs
Für jeden Benutzerlogin wird ein eigenes Logfile erstellt.
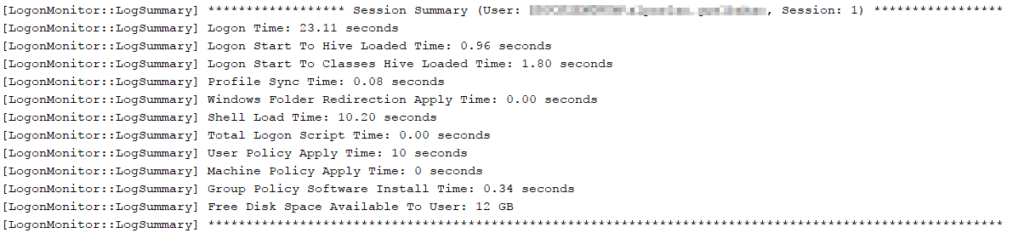
Über den Inhalt wird dann erkenntlich, welche Schritte die Loginzeit beeinflusst haben:
2017-08-28T08:29:45.367 TRACE (0e70-06b8) [LogonMonitor::ProcessUserPolicyEvent] User Policy Worker Started. Session: 1
2017-08-28T08:29:45.383 TRACE (0e70-0efc) [LogonMonitor::UserPolicyEventWorker] About To Wait for Profile Load Event
2017-08-28T08:29:45.383 TRACE (0e70-0efc) [LogonMonitor::UserPolicyEventWorker] Wait for Profile Load Event Returned
2017-08-28T08:29:45.383 TRACE (0e70-0efc) [LogonMonitor::UserPolicyEventWorker] About To Wait for Shell Loaded Event
2017-08-28T08:29:45.383 TRACE (0e70-06b8) [LogonMonitor::ProcessGroupPolicyEvent] Event Id: 5016, ActivityID: {15F206D6-862F-4FDC-9AE4-995E55A7B490}, Account: , Session: 1
2017-08-28T08:29:45.821 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: svchost.exe, Process Id: 1356, Parent Process Id: 640, Session: 1
2017-08-28T08:29:45.821 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: sihost.exe, Process Id: 1404, Parent Process Id: 952, Session: 1
2017-08-28T08:29:45.821 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: taskhostw.exe, Process Id: 2652, Parent Process Id: 952, Session: 1
2017-08-28T08:29:45.821 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: taskhostw.exe, Process Id: 3656, Parent Process Id: 952, Session: 1
2017-08-28T08:29:45.821 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: wscript.exe, Process Id: 4980, Parent Process Id: 952, Session: 1
2017-08-28T08:29:46.961 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: SearchProtocolHost.exe, Process Id: 612, Parent Process Id: 3776, Session: 1
2017-08-28T08:29:48.211 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: conhost.exe, Process Id: 1964, Parent Process Id: 4660, Session: 1
2017-08-28T08:29:48.211 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: powershell.exe, Process Id: 2492, Parent Process Id: 4980, Session: 1
2017-08-28T08:29:48.211 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: explorer.exe, Process Id: 3380, Parent Process Id: 4156, Session: 1
2017-08-28T08:29:48.211 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: wssm.exe, Process Id: 3656, Parent Process Id: 560, Session: 1
2017-08-28T08:29:48.211 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: userinit.exe, Process Id: 4156, Parent Process Id: 560, Session: 1
2017-08-28T08:29:48.211 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: vmwAgent.exe, Process Id: 4556, Parent Process Id: 1644, Session: 1
2017-08-28T08:29:48.211 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: vmlm_helper.exe, Process Id: 4660, Parent Process Id: 560, Session: 1
2017-08-28T08:29:49.243 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: cmd.exe, Process Id: 3572, Parent Process Id: 4156, Session: 1
2017-08-28T08:29:49.243 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: conhost.exe, Process Id: 5216, Parent Process Id: 2492, Session: 1
2017-08-28T08:29:49.243 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: rundll32.exe, Process Id: 5264, Parent Process Id: 368, Session: 1
2017-08-28T08:29:49.243 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: KIX32.EXE, Process Id: 5716, Parent Process Id: 3572, Session: 1
2017-08-28T08:29:49.243 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: conhost.exe, Process Id: 808, Parent Process Id: 3572, Session: 1
2017-08-28T08:29:50.278 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: pc-client.exe, Process Id: 6048, Parent Process Id: 6020, Session: 1
2017-08-28T08:29:50.282 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: KIX32.EXE, Process Id: 6072, Parent Process Id: 3572, Session: 1
2017-08-28T08:29:51.298 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: set-userpic.exe, Process Id: 4840, Parent Process Id: 3572, Session: 1
2017-08-28T08:29:51.313 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: rundll32.exe, Process Id: 5184, Parent Process Id: 5516, Session: 1
2017-08-28T08:29:55.392 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: backgroundTaskHost.exe, Process Id: 5560, Parent Process Id: 780, Session: 1
2017-08-28T08:29:55.392 TRACE (0e70-03b0) [WMIEventSink::HandleProcessCreation] Process Started: Name: RuntimeBroker.exe, Process Id: 5624, Parent Process Id: 780, Session: 1
2017-08-28T08:29:55.892 TRACE (0e70-11c4) [LogonMonitor::ShellLoadWorker] Found Taskbar. Session: 1
2017-08-28T08:29:55.892 TRACE (0e70-11c4) [LogonMonitor::SetShellLoadEndTime] Set Shell Load End Time. Session: 1
2017-08-28T08:29:55.892 TRACE (0e70-0efc) [LogonMonitor::UserPolicyEventWorker] Wait for Shell Loaded Event Returned
2017-08-28T08:29:55.892 TRACE (0e70-11c4) [LogonMonitor::GetUserProfileType] User Profile Type (2): Roaming. Session: 1
2017-08-28T08:29:55.892 TRACE (0e70-11c4) [LogonMonitor::GetUserProfilePath] Local Profile Path: C:\Users\user.name. Session: 1
2017-08-28T08:29:55.892 TRACE (0e70-11c4) [LogonMonitor::GetUserProfilePath] Key Path: SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-141383358-124726640-2919435464-1248. Session: 1
2017-08-28T08:29:55.892 TRACE (0e70-11c4) [LogonMonitor::GetUserProfilePath] Romaing Profile Path: \\storagepath\View-Users\user.name.V6. Session: 1
2017-08-28T08:29:55.892 TRACE (0e70-0efc) [LogonMonitor::StopWMIEventSink] WMI Event Sink Stopped, Session: 1
2017-08-28T08:29:56.360 TRACE (0e70-0efc) [LogonMonitor::StopSensEventSink] SENS Event Sink Stopped, Session: 1
2017-08-28T08:29:56.360 TRACE (0e70-0efc) [LogonMonitor::SetLogonEndTime] Set Logon End Time. Session: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetSessionStartToLogonStartTime] Session Start To Logon Time: 2260.30 seconds, Session: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetShellLoadTime] Shell Load Time: 10.95 seconds. Session: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetWFRApplyTime] Windows Folder Redirection Apply Time: 0.00 seconds. Session: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetProfileSyncTime] Profile Sync Time: 0.08 seconds. Session: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetMachineGPOTime] Machine Policy Time: 0 seconds. Session: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetUserGPOTime] Group Policy Software Installation Processing Asynchronous: True, Sessiond: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetUserGPOTime] GPO List Changed: True, Session: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetUserGPOTime] Group Policy Software Installation Time: 0.38 seconds, Error Code: 0, Session: 1
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetUserGPOTime] User Policy Time: 10 seconds. Session: 1
2017-08-28T08:29:56.360 TRACE (0e70-0efc) [LogonMonitor::IsGPLogonScriptSynchronous] Computer: Run these programs at user logon: Not Configured
2017-08-28T08:29:56.360 TRACE (0e70-0efc) [LogonMonitor::IsGPLogonScriptSynchronous] User: Run these programs at user logon: Not Configured
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::IsGPLogonScriptSynchronous] Group Policy Logon Scripts Are Asynchronous
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetGPLogonScriptTime] Group Policy Logon Script Time: 0.00 Seconds
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetGPLogonScriptTime] Group Policy PowerShell Logon Script Time: 0.00 Seconds
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::GetGPLogonScriptTime] Total Group Policy Logon Script Time: 0.00 Seconds
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::CheckGroupPolicySettings] Always wait for the network at computer start and logon: Not Configured
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::CheckGroupPolicySettings] Machine: Run these programs at user logon: Not Configured
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::CheckGroupPolicySettings] User: Run these programs at user logon: Not Configured
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::CheckGroupPolicySettings] Wait for remote user profile: Not Configured
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::CheckGroupPolicySettings] Set maximum wait time for network if a user has a roaming profile or remote home directory: Not Configured
2017-08-28T08:29:56.360 INFO (0e70-0efc) [LogonMonitor::CheckGroupPolicySettings] Specify network directories to sync at logon, logoff time only: Not Configured
2017-08-28T08:29:56.360 TRACE (0e70-0efc) [LogonMonitor::UserPolicyEventWorker] About to Wait For Shell Load Worker
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::LogProfileSize] Profile Size: 212.89MB, Files: 2286, Folders: 1160. Session: 1
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::LogProfileSize] File Size Distribution For Session 1:
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::LogProfileSize] 0 to < 1MB: 2234
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::LogProfileSize] 1MB to < 10MB: 49
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::LogProfileSize] 10MB to < 100MB: 3
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::LogProfileSize] 100MB to < 1GB: 0
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::LogProfileSize] 1GB to < 10GB: 0
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::LogProfileSize] >= 10GB: 0
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::GetDiskMetrics] Disk Space Metrics For User Profile Volume:
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::GetDiskMetrics] Disk Space Available To User: 12 GB
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::GetDiskMetrics] Free Disk Space: 12 GB
2017-08-28T08:30:11.330 INFO (0e70-11c4) [LogonMonitor::GetDiskMetrics] Total Disk Space: 31 GB
2017-08-28T08:30:11.330 TRACE (0e70-11c4) [LogonMonitor::ShellLoadWorker] Shell Load Monitor Exiting. Session: 1
2017-08-28T08:30:11.330 TRACE (0e70-0efc) [LogonMonitor::UserPolicyEventWorker] Wait for Shell Load Worker Returned
2017-08-28T08:30:11.330 INFO (0e70-0efc) [LogonMonitor::GetLogonTime] Logon Time: 24.67 seconds, Session: 1
2017-08-28T08:30:11.361 DEBUG (0e70-0efc) [LogonMonitor::PostToView] Broadcast timings to View Agent, SessionId: 1
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] ****************** Session Summary (User: DOMAIN\user.name, Session: 1) *****************
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Logon Time: 24.67 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Logon Start To Hive Loaded Time: 1.02 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Logon Start To Classes Hive Loaded Time: 1.89 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Profile Sync Time: 0.08 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Windows Folder Redirection Apply Time: 0.00 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Shell Load Time: 10.95 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Total Logon Script Time: 0.00 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] User Policy Apply Time: 10 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Machine Policy Apply Time: 0 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Group Policy Software Install Time: 0.38 seconds
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] Free Disk Space Available To User: 12 GB
2017-08-28T08:30:11.361 INFO (0e70-0efc) [LogonMonitor::LogSummary] ********************************************************************************************************
Automatische Analyse per Skript
Leider werden die Werte bislang nur in Form der eben gezeigten Log-Dateien vorgehalten. Ein Abfragen über eine Schnittstelle/API fehlt komplett. Auch ist es nicht möglich die Werte z.B. über Umgebungsvariablen auszulesen.
Deswegen habe ich ein Skript in Powershell geschrieben, welches die Logdateien auswertet und die wichtigsten Werte anzeigt. Zusätzlich können die Werte in eine MSSQL Datenbank geschrieben werden um auch größere Mengen besser analysieren zu können.
Das Skript kann entweder eine einzelne Logdatei im Stil des VMware Log Monitor analysieren oder gleich ganze Ordner mit mehreren Dateien. Ihr könnt das Skript entweder kopieren oder hier herunterladen. VMwareLogonMonitor2MSSQLv2.ps1
Falls jemand Fehler findet oder sich Verbesserungsvorschläge ergeben, könnt ihr mir gerne einen Kommentar hinterlassen.
<#
.NOTES
===========================================================================
Created with: SAPIEN Technologies, Inc., PowerShell Studio 2015 v4.2.81
Created on: 28.08.2017 13:39
Created by: Constantin Lotz
Organization:
Filename: VMWareLogonMonitor2MSSQL.ps1
===========================================================================
.DESCRIPTION
Die Software liest die Log-Dateien des VMware Login Monitor aus und trägt die relevanten Daten in eine SQL-Datenbank
This software reads out the logfiles produced by VMware Logon Monitor which is included in VMware Horizon (View) 7.2
and pushs them into an Microsoft SQL Database
.CHANGELOG
28.02.2018 # Switch onlyTextOutput does not work when Database connection is invalid. Skipped the connection startup when the switch is set
# Thanks to Richard
The needed MSSQL Schema for storing Data:
### Start ###
/****** Object: Table [dbo].[VmwareLogonMonitorStats] Script Date: 08/29/2017 15:46:36 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
SET ANSI_PADDING ON
GO
CREATE TABLE [dbo].[VmwareLogonMonitorStats](
[UniqueID] [varchar](100) NOT NULL,
[LogonTimeSec] [float] NOT NULL,
[ProfileSyncTimeSec] [float] NULL,
[TotalLogonScriptSec] [float] NULL,
[MachinePolicyApplySec] [float] NULL,
[LogonStartHiveSec] [float] NULL,
[LogonStartClassesHiveSec] [float] NULL,
[FreeDiskSpaceGB] [int] NULL,
[ShellLoadTimeSec] [float] NULL,
[GPOSoftwareInstallSec] [float] NULL,
[UserPolicyApplySec] [float] NULL,
[WindowsFolderRedirectionSec] [float] NULL,
[LogonDateTime] [datetime] NULL,
[UserName] [varchar](50) NULL,
[ProfileSizeMB] [float] NULL,
[ProfileSizeFiles] [int] NULL,
[ProfileSizeFolders] [int] NULL,
CONSTRAINT [PK_VmwareLogonMonitorStats] PRIMARY KEY CLUSTERED
(
[UniqueID] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
SET ANSI_PADDING OFF
GO
### End ###
#>
param (
[Parameter(Position = 0, ValueFromPipeline = $true)]
[String]$logonMonitorFolder,
[Switch]$onlyTextOutput
)
# Display Help
if (!$logonMonitorFolder) {
Write-Host "######################################"
Write-Host "## VMWareLogonMonitor2MSSQL.ps1"
Write-Host "## Version: 0.1"
Write-Host "## (c) Constantin Lotz"
Write-Host "## www.constey.de | VLM@constey.de"
Write-Host "######################################"
Write-Host "## - Requieres Powershell v3 -
Write-Host "## To Scan a complete folder with multiple Logfiles"
Write-Host "## .\VMwareLogonMonitor2MSSQL.ps1 <VMWareLogonMonitorLogFolder>"
Write-Host "## To Scan only one specific Logfile"
Write-Host "## .\VMwareLogonMonitor2MSSQL.ps1 <Logfile>"
Write-Host "## Change MSSQL Login Data within Script under 'Open SQL Connection'"
Write-Host "## If you only want Textoutput without writing to MSSQL add -onlyTextOutput Parameter"
Write-Host "########### exiting... ############"
exit (0)
}
# Maybe not needed
if ($logonMonitorFolder.EndsWith("\") -eq $true)
{
$logonMonitorFolder = $logonMonitorFolder + "*.txt"
} elseif ($logonMonitorFolder.EndsWith(".txt") -eq $false)
{
$logonMonitorFolder = $logonMonitorFolder + "\*.txt"
}
# Parameters
$logfile = $PSScriptRoot + "\VmwareLogonMonitor.log"
$logtime = get-date -format 'dd.MM.yyyy;HH:mm:ss'
$dataArray = New-Object System.Collections.ArrayList
# Open SQL Connection
$dataSource = "hostname" # Hostname or IP-Adress
$user = "sql-username" # SQL Username
$pwd = "password" # SQL Password
$database = "Databasename" # Database name
$connectionString = "Server=$dataSource;uid=$user; pwd=$pwd;Database=$database;Integrated Security=False;"
if ($onlyTextOutput -eq $true) {
# Do not connect when onlyTextOutput is set
} else {
$connection = New-Object System.Data.SqlClient.SqlConnection
$connection.ConnectionString = $connectionString
$connection.Open()
}
# Logging Function
function Write-Feedback()
{
param
(
[Parameter(Position = 0, ValueFromPipeline = $true)]
[string]$msg
)
Write-Host $msg;
$msg | Out-File $logfile -Append
}
# Regex Grabbing the Logfile
function ExtractDataFromLogfile ()
{
param
(
[Parameter(Position = 0, ValueFromPipeline = $true)]
[string]$logonfile
)
# Check if File exists
if (Test-Path $logonfile)
{
# Check if File is from VMware Logon Monitor
$content = Get-Content $logonfile | select-String -Pattern "VMWLogSettings"
if ($content.length -gt 0)
{
$uniqueID = gci $logonfile | % Name
$timeInSeconds = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Logon Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$username = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] \*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\* Session Summary \(User: (.*)," | ForEach-Object { $_.Matches.Groups[1].Value }
$computername = Select-String -path $logonfile -Pattern "\[VMWLogSettings\] Computer Name: (.*)" | ForEach-Object { $_.Matches.Groups[1].Value }
$logonStartHive = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Logon Start To Hive Loaded Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$logonStartClassesHive = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Logon Start To Classes Hive Loaded Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$profileSyncTime = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Profile Sync Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$windowsFolderRedirection = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Windows Folder Redirection Apply Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$shellLoadTime = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Shell Load Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$totalLogonScript = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Total Logon Script Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$userPolicyApply = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] User Policy Apply Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$machinePolicyApply = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Machine Policy Apply Time:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$gpoSoftwareInstall = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Group Policy Software Install Time: \s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$freeDiskSpace = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogSummary\] Free Disk Space Available To User:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
$logonDateTime = Select-String -path $logonfile -Pattern "([^\s]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | Select-Object -first 1
$profileSize = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogProfileSize\] Profile Size:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % ToString([cultureinfo]::GetCultureInfo('en-US'))
[int]$profileSizeFiles = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogProfileSize\] Profile Size: .* Files:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value }
[int]$profileSizeFolders = Select-String -path $logonfile -Pattern "\[LogonMonitor::LogProfileSize\] Profile Size: .* Files: .* Folders:\s*([\d|.]+)" | ForEach-Object { $_.Matches.Groups[1].Value } | % trim (".")
$values = @{
"UniqueID" = $uniqueID;
"LogonDateTime" = $logonDateTime;
"LogonTime" = $timeInSeconds;
"UserName" = $username;
"ComputerName" = $computername;
"LogonStartHive" = $logonStartHive;
"LogonStartClassesHive" = $logonStartClassesHive;
"ProfileSyncTime" = $profileSyncTime;
"WindowsFolderRedirection" = $windowsFolderRedirection;
"ShellLoadTime" = $shellLoadTime;
"TotalLogonScript" = $totalLogonScript;
"UserPolicyApply" = $userPolicyApply;
"MachinePolicyApply" = $machinePolicyApply;
"GPOSoftwareInstall" = $gpoSoftwareInstall;
"FreeDiskSpace" = $freeDiskSpace;
"ProfileSize" = $profileSize;
"ProfileSizeFiles" = $profileSizeFiles;
"ProfileSizeFolders" = $profileSizeFolders;
}
# Write to Variable for no text output
$temp = $dataArray.Add($values)
}
}
else
{
# File does not exist
Write-Feedback "$logtime - Fehler: Datei existiert nicht. - Datei: $($logonfile)"
}
}
# Check if runs for a folder or only for a File
if (($logonMonitorFolder.EndsWith(".txt") -eq $true) -and ($logonMonitorFolder.EndsWith("*.txt") -eq $false))
{
ExtractDataFromLogfile $logonMonitorFolder
}
else
{
foreach ($file in Get-ChildItem $logonMonitorFolder)
{
ExtractDataFromLogfile $file
}
}
if ($onlyTextOutput -eq $true)
{
# Just Output the Data
$dataArray
}
else
{
# Push Data into MSSQL Database
foreach ($entry in $dataArray)
{
# #Write to SQL
$cmd = New-Object System.Data.SqlClient.SqlCommand
$cmd.connection = $connection
try
{
$cmd.commandtext = "INSERT INTO dbo.VmwareLogonMonitorStats (UniqueID,LogonDateTime,UserName,LogonTimeSec,ProfileSyncTimeSec,TotalLogonScriptSec,MachinePolicyApplySec,LogonStartHiveSec,LogonStartClassesHiveSec,FreeDiskSpaceGB,ShellLoadTimeSec,GPOSoftwareInstallSec,UserPolicyApplySec,WindowsFolderRedirectionSec,ProfileSizeMB,ProfileSizeFiles,ProfileSizeFolders)
VALUES('{0}','{1}','{2}',{3},{4},{5},{6},{7},{8},{9},{10},{11},{12},{13},{14},{15},{16})" -f $entry.UniqueID, $entry.LogonDateTime, $entry.UserName, $entry.LogonTime, $entry.ProfileSyncTime, $entry.TotalLogonScript, $entry.MachinePolicyApply, $entry.LogonStartHive, $entry.LogonStartClassesHive, $entry.FreeDiskSpace, $entry.ShellLoadTime, $entry.GPOSoftwareInstall, $entry.UserPolicyApply, $entry.WindowsFolderRedirection, $entry.ProfileSize, $entry.ProfileSizeFiles, $entry.ProfileSizeFolders
# Write-Host $cmd.CommandText
$result = $cmd.executenonquery()
if ($result -eq 1)
{
Write-Feedback "$logtime - Info: Die Meldung: $($entry.UniqueID) - wurde eingetragen."
}
}
catch
{
Write-Feedback "$logtime - Fehler: $($entry.UniqueID)"
# More detailed
#Write-Feedback "$logtime - Fehler: $($cmd.commandtext) - Datei: $($error)"
}
}
}
# Closing open Database connections
if ($onlyTextOutput -eq $true) {
# Do not close when onlyTextOutput is set
} else {
$connection.Close()
}
# End
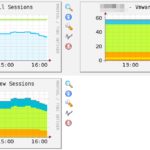
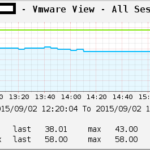
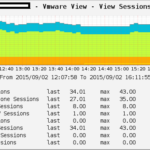
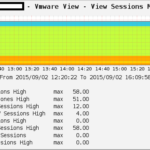
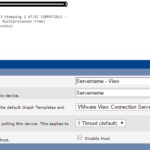
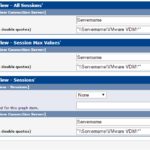
 Wie vielleicht so manche Beiträge hier vermuten lassen, setze ich VMware Horizon View zur Desktopbereitstellung ein. So hat sich mir die Frage gestellt ob man nicht die Anzahl an Connections, gestarteten Desktops etc. im MRTG bzw. Cacti überwachen kann.
Wie vielleicht so manche Beiträge hier vermuten lassen, setze ich VMware Horizon View zur Desktopbereitstellung ein. So hat sich mir die Frage gestellt ob man nicht die Anzahl an Connections, gestarteten Desktops etc. im MRTG bzw. Cacti überwachen kann.